Introduction
Over the past year, I have heard about this new Flipper Zero device. The Flipper Zero was initially announced in 2020 and has recently been getting attention from people on social media platforms. When I first saw a video of the Flipper Zero emulating remotes for a projector and setting off the need assistance notification in Walgreens stores. From that moment on, I instantly knew I wanted to get my hands on one and figure out what it is capable of.

About the Flipper Zero
The Flipper Zero is a small “hacking” device that costs $169 and comes out of the box with many features. Some of the features are but are not limited to…
- Sub-1 gigahertz transceiver
- 125 kilohertz RFID
- NFC
- Bluetooth
- Infrared transceiver
- Micro SD card
- GPIO
- iButton
- Badusb
All these built-in features allow you to do quite a bit regarding cyber security. You can use the Flipper with additional applications to brute force an RFID scanner to get past a keycard reader. You can use the sub-1 gigahertz transceiver to send signals to open doors that you may need specific codes to open. One way to think about this feature is how a garage door or doorbell work, Most of the time, you hit the button on one end that sends a specific code that activates the device on the other end. Another popular feature of the Flipper Zero is the infrared transceiver. With this feature, you can send signals the same way a tv remote can through light. This feature is pretty fun to mess with. I have been able to emulate my family’s tv remote and turn off the tv without the remote. Another device that commonly uses infrared is projectors, and I have been able to turn off the projectors around campus without the remote. Of course, all these features can work in the opposite way, where you can read RFID, sub-1 gigahertz, and infrared. All of these features are pretty cool, but there is one that has gained my interest in a more significant way.
My Favorite Feature
Over the past month of working with my Flipper Zero, I have come to enjoy the bad USB feature. Badusb is a feature on the Flipper that allows you to plug in the Flipper to emulate a computer’s keyboard and “type” commands or do any action that a regular keyboard would be able to perform. Badusb seems like a relatively harmless gimmick until you realize what kind of power a keyboard has. Most people understand that there are many shortcuts that you can do with a keyboard to increase the productivity of your workflow. However, with the right tools like a USB Rubber Ducky, O.MG device, or a Flipper Zero, we can do quite a bit with the right tools. Starting off, if you intend to start messing with USB keystroke injection, ensure you know what the script you intend to run does. There are many scripts that I have found that will cause permanent damage to an operating system.
Programming For Bad USB
Some of the more recent Badusb devices, like the USB Rubber Ducky, O.MG devices, and of course, the Flipper Zero, will be programmed using DuckyScript. Ducky is a straightforward language to learn because of how simple the syntax is. To give you a good example of some Ducky code, I wrote a quick script that saves a message to the desktop.
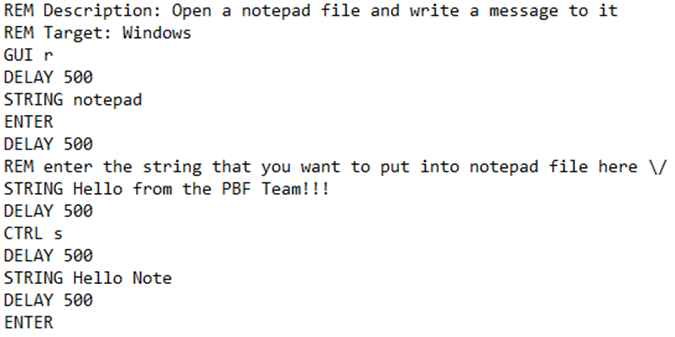
When looking at this code, for the most part, you can see exactly what the program will do. The comments at the top of the file, signified by the REM delimiter, briefly describe what the program does and what type of operating system this script is designed for. The other harder-to-understand delimiter for this program is the “GUI” command towards the top of the file, and all that does is simulate pressing the Windows key with the added “r” keystroke to pull up the run dialog for Windows. There is essentially no limit to what you can do from this menu with the proper privileges. You can pull up any application, including Powershell and command prompt.
What Does This Mean for Penetration Testers
The significance of having access to Powershell and command prompt means that attackers could download more or less anything they want onto the target computer using programs like curl. Using curl, I could send a file with password information from a target computer over the internet to a self-hosted web server. Or, to make it even easier, you can use webhooks to do the same thing making it super easy to exfiltrate data from targeted computers. Sometimes the penetration tester or attacker doesn’t even need to be on-site to commit these types of attacks. All an attacker needs is someone else to be curious enough to figure out what could be on a planted malicious USB drive.
Drawbacks to Badusb
Badusb is a fantastic idea, but there is one huge problem with actually being able to run these scripts, and that is having physical access to these USB ports. One of the easiest ways to prevent these types of attacks is to keep computers behind locked doors. This causes just a little bit of trouble for the attacker because the only way that this kind of attack works is if there is access to USB ports. Another way to mitigate these types of attacks is to be aware of this kind of attack. A planted USB drive would be useless if an employee followed proper protocol and took the USB drive to someone who could adequately deal with the drive. Another way is to buy a malicious USB or detector that can detect if a USB is trying to input keystrokes to the computer and block any data being injected into the computer.
The Potential of a Flipper Zero
With all the cool built-in features put aside, some of the true potential of the Flipper is found in its open-source nature and support for the device by the Flipper Zero community. There are many different applications that are not built into the device but are already available because of the community that follows this device. If you need an application that does some specific task, there is also nothing stopping you from taking the time to develop an application for the Flipper. Not to mention the capabilities of the GPIO, where you can buy or create modules that can extend the device’s capabilities. One of the Flipper Zero OEM modules is the WiFi Devboard which can allow for additional features such as WiFi penetration testing and allowing the Flipper to connect to the internet directly. There is an endless amount of capability for this little device as long as the community is still developing for the Flipper Zero. Even if all of the hardware becomes outdated, people can still make these modules to attach to the Flipper.
