What is an API?
An API (Application Programming Interface) is a set of protocols and definitions that enable third parties to interface with services and servers hosted by someone else, provided they support an API. To name a few, this includes Reddit’s Apollo (R.I.P.), DIM’s Destiny’s browser item manager, legendary Twitter account Pepito the Cat, and Discord bots. According to API security company FireTail, over 83% of internet traffic is API calls, and this value continues to increase. The commodity of API usage provides a massive attack surface, and poorly secured or misconfigured APIs could easily provide an attacker a foothold in a victim’s infrastructure or network.
Google Maps API
One popular API integration is Google Maps. By utilizing Google’s Maps API, third parties can interface and embed the expansive and interactive map into their websites. Despite the benefits, this does not come for free. Google charges differently according to what API call is used per 1000 calls. The pricing for maps, routes, and places can be found here.
Restricted vs. unrestricted keys
For Google Maps, its API key, or method of authenticity to access the resource, needs to be hard-coded into the website. This alone is a security problem but can be remediated by using a restricted API key. A restricted key only works on certain or specified web pages, preventing random users from copying and reusing the key elsewhere.
However, a common misconfiguration emerges when someone mistakenly hard-codes an unrestricted API key into the website’s source. Unlike its restricted counterpart, unrestricted keys can be copied and reused anywhere. If an unrestricted API key is obtained, an attacker can make arbitrary calls under someone else’s account.
Exploitation
The following demonstration is only intended for educational use. Before continuing with the example, it must be emphasized that this is a form of cyber attack, and engaging in these actions upon a network with which you do not have authorization to manipulate is illegal. If you were to follow along, only proceed with full certainty you have permission.
Keyhacks
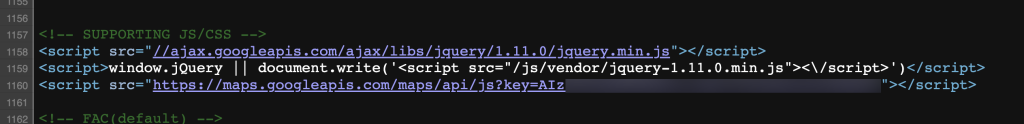
Exploiting this misconfiguration is as simple as viewing a website’s source. If a Google Maps API key is found, there are many ways to determine if it’s restricted or unrestricted. I used Streaak’s Keyhacks tool, full of various URL templates for testing keys. Similar output to the following will determine an unrestricted API key has been found:

If a restricted API key is inputted, the server will return with an error message indicating the key is invalid.

gmapsapiscanner
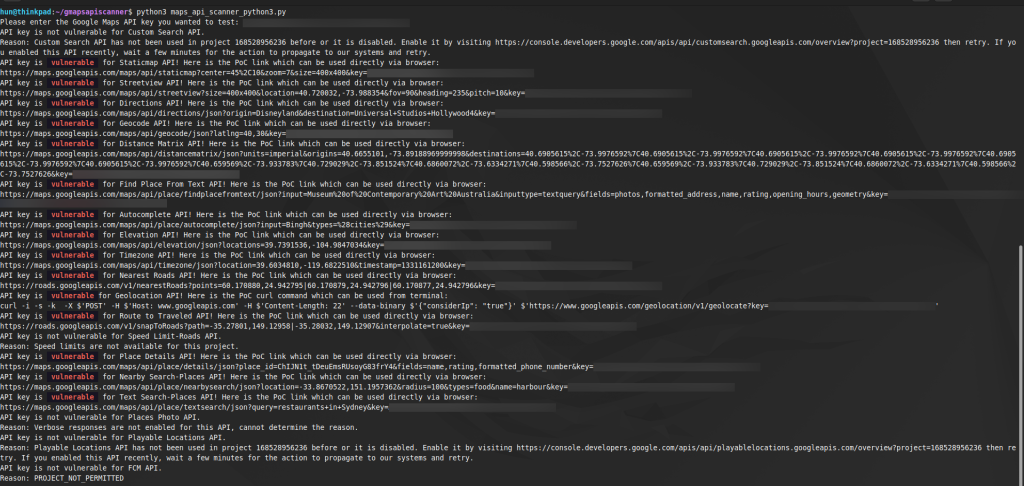
Another great method for testing keys is to use Ozguralp’s Google Maps API Scanner, a terminal-based tool. This is a more automated way to test many of the URLs previously used manually. If a call is successful, the tool reports the key as “vulnerable” in that area.
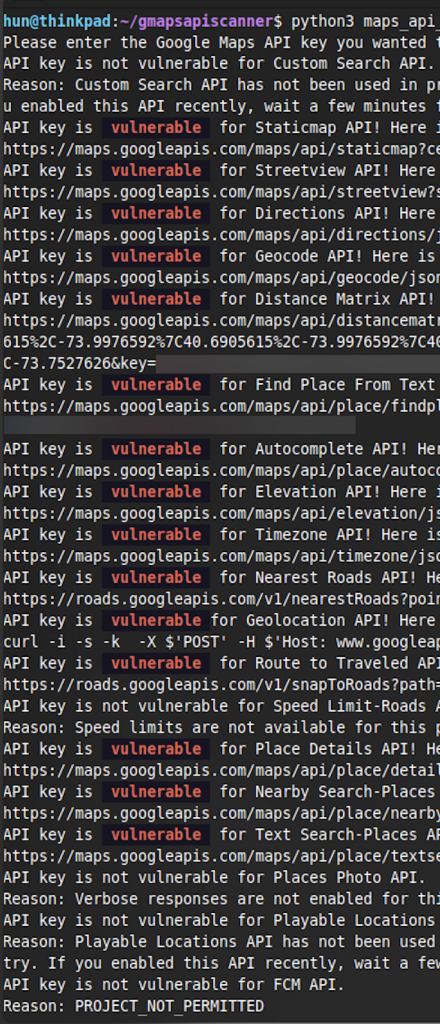
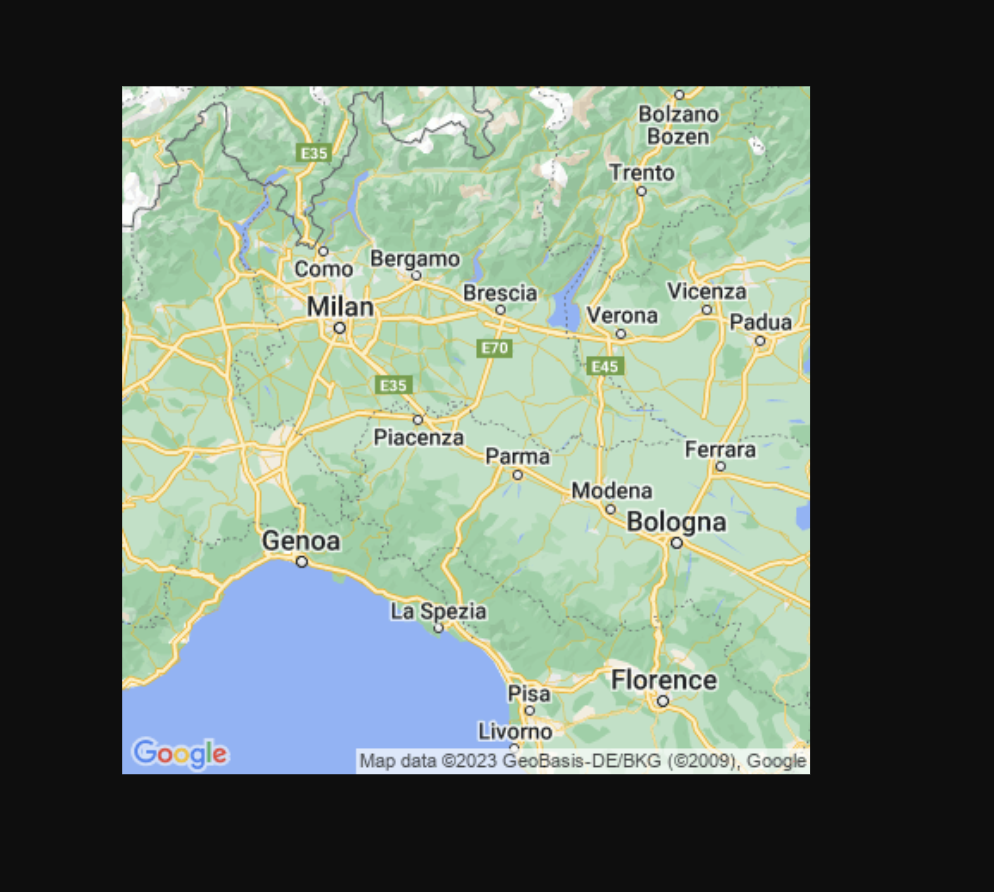
Custom HTML
For a proof-of-concept, I think building a basic HTML page with the Google Maps embed and interacting with it is the most impactful demonstration of compromise.
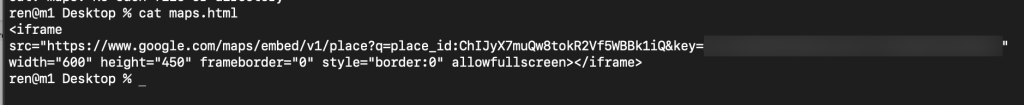
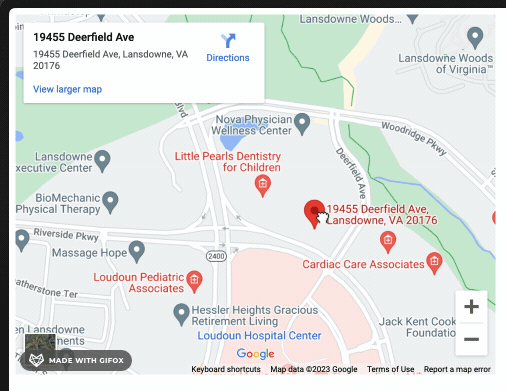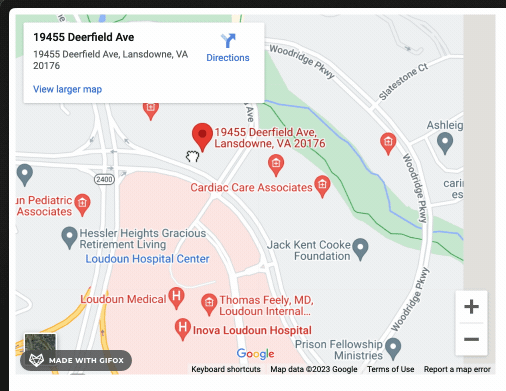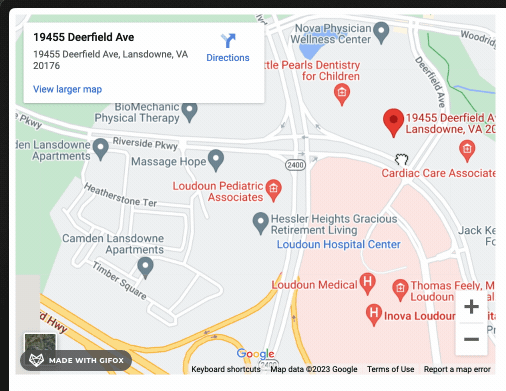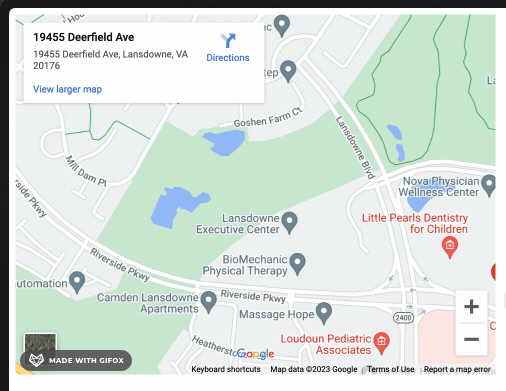
Damage and protection
While it’s cool that it’s possible to make arbitrary Google Maps API calls under someone else’s account, what damage is being done? Remember, Google charges for their API usage, and it varies relative to how many calls are made. The two primary methods for paying are pay-as-you-go and setting a quota. Google describes it in more detail here.
If an attacker were to build a simple tool that floods API calls under someone else’s account, two things are likely to occur:
- If the victim uses the pay-as-you-go model, they will be charged infinitely, which could render massive financial damage.
- If the victim has a quota set, all API calls will cease to work until the next period, resulting in a denial-of-service attack against Google’s integrations on the victim’s websites. This could impact a single page to thousands of websites depending on their infrastructure.
Luckily, if you are using Google Maps integrations, protecting yourself is as simple as generating a restricted API key and utilizing that instead, and Google provides a fantastic walkthrough that can be found here. For peace of mind, the offensive tools demonstrated are also fantastic resources for validating such API keys are properly configured.
References
- https://www.redhat.com/en/topics/api/what-are-application-programming-interfaces
- https://www.businesswire.com/news/home/20230510005193/en/FireTail-API-Security-Report-2023-On-Track-for-Record-Year-Of-API-Breaches#:~:text=Over%2083%25%20of%20internet%20traffic,up%20to%2025%20API%20calls
- https://apolloapp.io/
- https://destinyitemmanager.com/en/
- https://twitter.com/pepitothecat
- https://mapsplatform.google.com/pricing/
- https://github.com/streaak/keyhacks
- https://github.com/ozguralp/gmapsapiscanner
- https://developers.google.com/maps/documentation/javascript/usage-and-billing#set-caps
- https://developers.google.com/maps/api-security-best-practices#restricting-api-keys
