What is Active Directory?
Active Directory is a proprietary directory service developed by Microsoft. First implemented in Windows 2000 Server, Active Directory was built to simplify and centralize the management of users, systems, and network resources in a domain. What once was a previously arduous task is now integrated, scalable, and fast.
However, within Active Directory is an outdated setting that, when enabled, allows an attacker to potentially compromise an entire domain with little to no credentials at all. Before discussing the exploitation of this vulnerability, the structure of Active Directory must be understood to highlight the severity of such an attack.
Centralized Administration
Active Directory assumes a hierarchal directory that contains information about users, systems, permissions, and other units within a particular network environment. The hierarchal design provides administrators with a centralized point of management, making it easier to organize, secure, and configure their domain. Active Directory is also scalable, simplifying the implementation and management of new and existing assets for networks of any size.
This doesn’t stop at a single network or domain, though. The three primary tiers of Active Directory are:
- Domain – a network of users, groups, computers, and other Active Directory objects.
- Tree – a collection of domains that share a contiguous namespace.
- Forest – a collection of domain trees that share a common scheme and have a trust relationship, which is like a link between two trees.
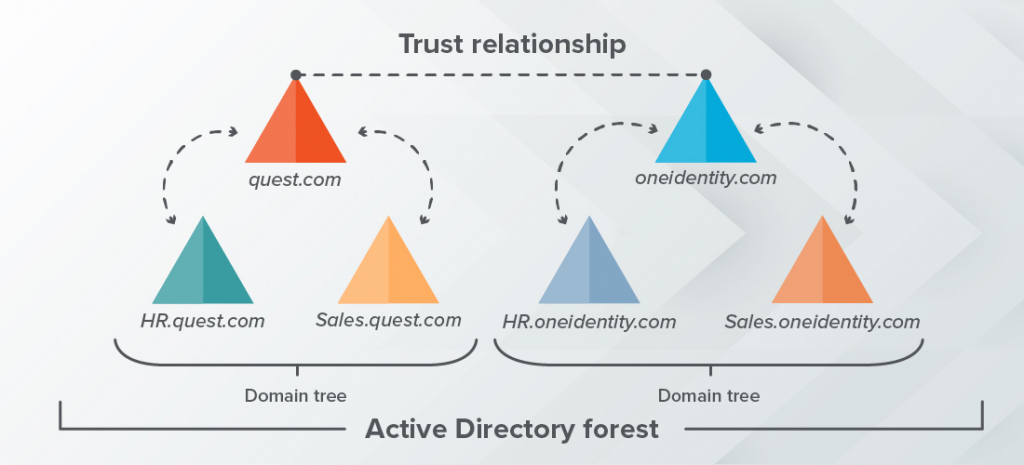
Primary Components of Active Directory
Domain Controllers
The main component of Active Directory is the Active Directory Domain Service (AD DS). Servers running AD DS are referred to as domain controllers, where each domain controller stores a copy of the entire domain directory, and if multiple controllers exist, they replicate and synchronize data with one another. Domain controllers also handle the authentication process, requiring users to authenticate themselves to access network resources.
Domain Name System (DNS)
Active Directory Domain Services uses Domain Name System (DNS) as a mechanism for locating the domain controller. DNS is a database of domain names that are resolved into IP addresses when queried. If clients or users on a network wish to communicate with a domain controller, DNS is used to find the location of the server without knowing the IP address.
DNS Fallbacks (LLMNR and NBNS)
If DNS were to go down for any reason, there are two fallback protocols that a system can use to resolve hostnames. Link-Local Multicast Name Resolution (LLMNR) if DNS is down, and NetBIOS Name Server (NBNS) if both DNS and LLMNR are down. In Active Directory, LLMNR is enabled by default and works by sending a query to all devices on the network, requesting its hostname such that the system can resolve other hosts.
Attacking LLMNR and NBNS
Man in the Middle
When LLMNR and NBNS broadcast their queries to the network, technically any host can reply, but in a traditional environment, the host being searched is the only machine to respond. An attacker on a network can leverage this and spoof, or impersonate, a certain machine on the network, where the victim may pass its hashed credentials to the attacker. From this, the attacker may open a connection to the actual destination machine and relay the victim’s traffic to it. This is called a man-in-the-middle (MITM) attack; or more specifically, an SMB relay attack.
Password Cracking
When an attacker receives the hashed password from a victim, they may also turn around and crack this password using a brute-force attack. If the attacker can crack the password, they now have plaintext credentials they can use elsewhere in the network to potentially escalate privileges or gain other sensitive information.
Tools for Attacking Active Directory
Responder is one of the most popular tools for attacking Active Directory and comes pre-installed in the free-to-download Kali Linux. Responder is best known for exploiting the man-in-the-middle vulnerability in LLMNR and NBNS, as well as gathering hashes from victim machines in the network.
To crack password hashes, a wordlist, or a file containing passwords found in data breaches, is passed into cracking tools like Hashcat or John the Ripper, also pre-installed in Kali Linux. If the password is weak or common, an attacker can gain plaintext credentials to escalate privileges throughout the network.
How to Protect Yourself
Active Directory is one of the most common domain services used in networks of all sizes, and this single vulnerability in LLMNR and NBNS can provide an attacker with zero authentication to escalate to full control over a domain or forest in a matter of days, sometimes even hours. If an attacker were to achieve this level of permission, they can do whatever they want with the network and the devices nested within it.
Disabling LLMNR
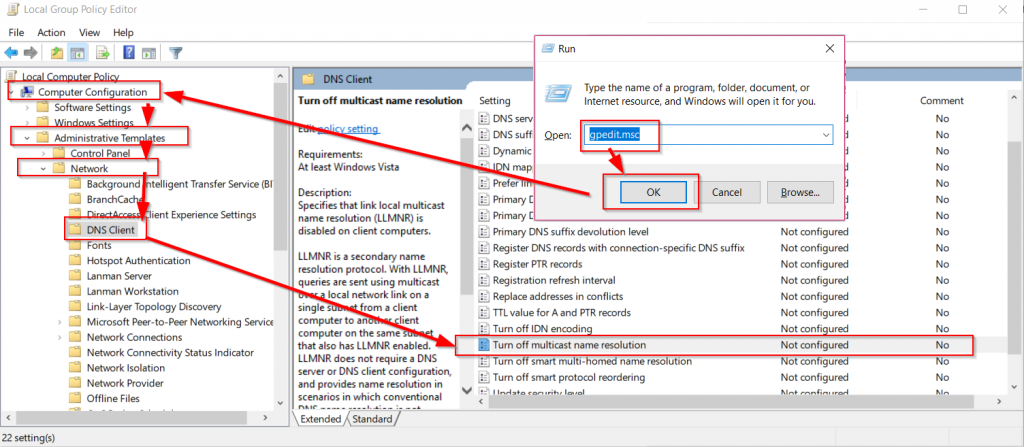
Protecting yourself from this kind of attack is easy. Disabling LLMNR is as simple as:
- Open Local Group Policy Editor on a domain controller
- Expand Computer Configuration
- Expand Network, and select DNS Client
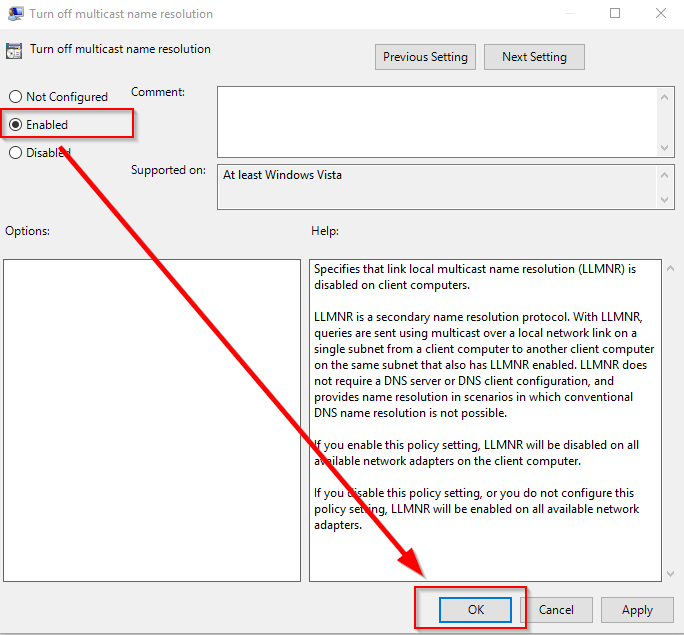
- Double-Click “Turn off multicast name resolution”
- Select “Enabled”
- Select OK
If every machine is connected to a single domain, this setting will synchronize to all clients and controllers. For machines not connected to the domain, manually repeat the previous steps for each device. For virtually all modern use cases, LLMNR does not need to be enabled.
If LLMNR is Required
Not all networks are created equal, and there are rare cases where disabling LLMNR is not an option. For these cases, ensure SMB version 1 is disabled, prioritizing SMB version 2 or SMB version 3. Any version higher than SMB version 1 is no longer vulnerable to SMB relay attacks, and Microsoft has a great listing regarding the many ways to approach securing SMB: https://learn.microsoft.com/en-us/windows-server/storage/file-server/troubleshoot/detect-enable-and-disable-smbv1-v2-v3?tabs=server
Resources
https://www.quest.com/solutions/active-directory/what-is-active-directory.aspx
/https://www.blackhillsinfosec.com/how-to-disable-llmnr-why-you-want-to/
https://www.advantio.com/blog/attacking-active-directory-by-llmnr-nbsn
